 |
| GET YOUR VIDEOS IN RECOMMENDED |
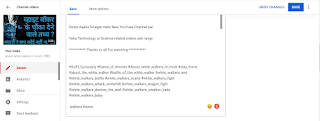
FOLLOWING STEPS TO UPLOAD YOUR VIDEO IN YOUTUBE
- OPEN CHROME (IN MOBILE USE DESKTOP MODE) GO TO YOUR CHANNELL.
2. GO TO YOUR VIDEOS THOSE UPLOADED.
3. CLICK ON EDIT ICON WHICH VIDEO YOU WANT.
4. YOU CAN EDIT HERE ALL WHICH CAN HELP YOUR VIDEOS EASLY TO FIND IN YOUTUBE.
5. HERE YOU HAVE TO CHANGE YOUR DESCRIPTION ACCORDING TO YOU AND ADD BEST TAGS THAT ENHANCE THE YouTube SEARCH KEYWORD SO PUT BEST TAGS HERE.
6. NOW YOUE HAVE TO ADD TAGS AFTER COMPLETED YOUR DESCRIPTION BOX.IN YOUR TAG SECTION BELOW THE DESCRIPTION YOU CAN SEE
7. YOU CAN SEARCH TAGS IN WEBSITES ACCORDING TO YOUR VIDEO BEST WAY USE YOUR YouTube SEARCH SECTION
8. FROM PlayStore YOU CAN DOWNLOAD TUBEBUDDY TubeBuddy app IT'S HELP TO GET SUGGESTION FOR TAGS
NOW YOU CAN SAVE YOUR VIDEO ABOVE OPTION:-



















Yes
ReplyDeleteIt's correct
How To Add Tags In Youtube Videos Get In Recomended Your Video
ReplyDelete-
Scifi Curoisity >>>>> Download Now
>>>>> Download Full
How To Add Tags In Youtube Videos Get In Recomended Your Video
-
Scifi Curoisity >>>>> Download LINK
>>>>> Download Now
How To Add Tags In Youtube Videos Get In Recomended Your Video
-
Scifi Curoisity >>>>> Download Full
>>>>> Download LINK